Luxembourgish landscape in information security threat through years (from Diagnostic NC3)
A Bit of Background History
The “unpleasant yield” of the evolution of technology and information systems is the increase of cyber-attacks and intensified risks and threats we should face. Such threats have been present since the dawn of information technology, yet their nature and ability to cause harm was different. Today’s cyberattacks are more sophisticated and destructive than ever before.
Methods used in the Study
This study summarizes the results of 149 NC3 Diagnostics, which have been carried out between 06/2016 and 12/2019. During this period, 1774 recommendations were given and 434 of them were considered as urgent to implement, which represents approximately 2.91 urgent recommendations per diagnostic. Throughout the diagnostics, 4768 questions were asked, and only 452 of them were answered completely which shows that the subject is not well-known.
Explanation of used metrics
- Success percentage: an optimised answer counts as 1 success, whereas a basic answer counts as 0.5.
- Dangerousness indicator: a fail of answering a question combined with a NC3 coefficient used for questions in the NC3 Diagnostic.
- Recommendation percentage: the percentage of Diagnostics where a certain recommendation was given
The top 10 danger factors in the last years
Over the past years, NC3 has been collecting a vast amount of data on the most important risk factors in startups and SMEs. During such quick assessments, many different categories have been discussed and assessed. The below table shows the top 10 danger factors identified by the NC3 Diagnostic over the past couple of years:
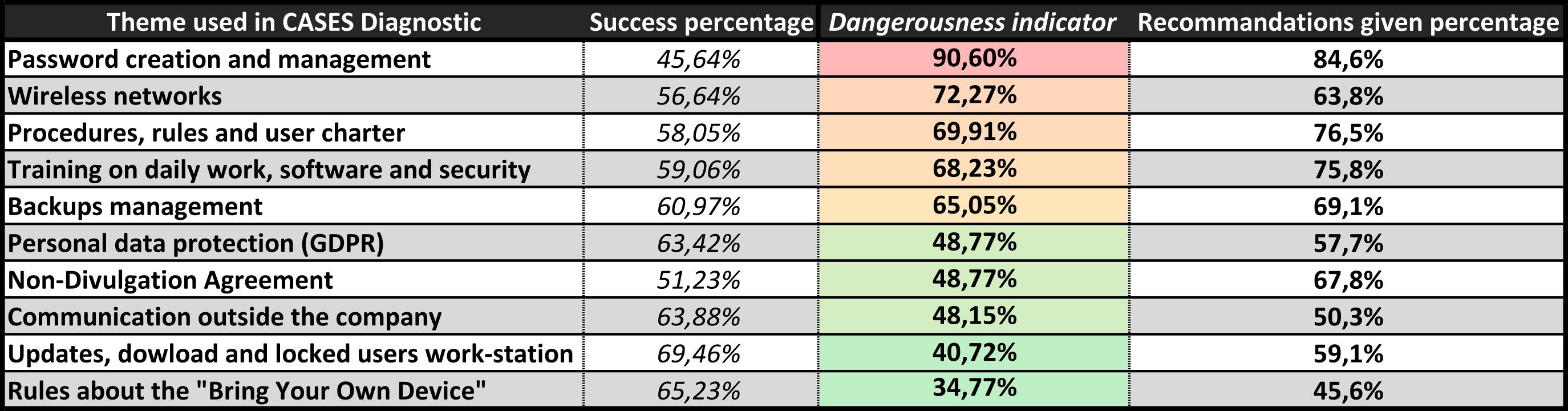
Table 1 - The Top 10 Dangerousness Indicators found by NC3 Diagnostic
“Password creation and management” includes length and type of passwords, whereas “Wireless networks” comprise configuration related matters besides password management. “Backup management” involves backup periodicity, location, and restoration of backups. We refer to “Non-Disclosure Agreement” on confidentiality clauses in contracts, while “BYOD” means the accepted practice of employees being allowed to use their own device/s for professional work at their workplace or when working from home.
These factors need special attention. Password creation and management is a subject which is often repeated, and the dangerousness indicator shows why it’s important to have some heavy protection for users or local networks. Rules, trainings and backups are importants subjects that shouldn’t be ignored.
Evolution of 3 important factors between 2016 and 2019
The below table shows the “Dangerousness Indicator” figures in the percentage of 3 importants factors between 2016 and 2019. The numbers are straight forward, especially concerning the password creation and management. Password-related threats are one of the most serious threats according to the NC3 Diagnostic.
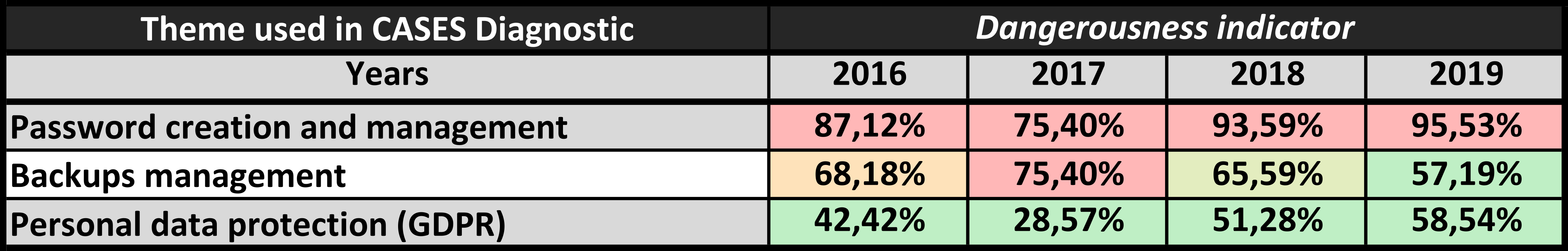
Table 2 - Evolution of important factors throughout 2016-19
The below line graph represents the above tables visually. The horizontal axis represents the period of 2016-2019, whereas the vertical axis shows the values of the 3 important cybersecurity threats in percentages of the Dangerousness Indicator.
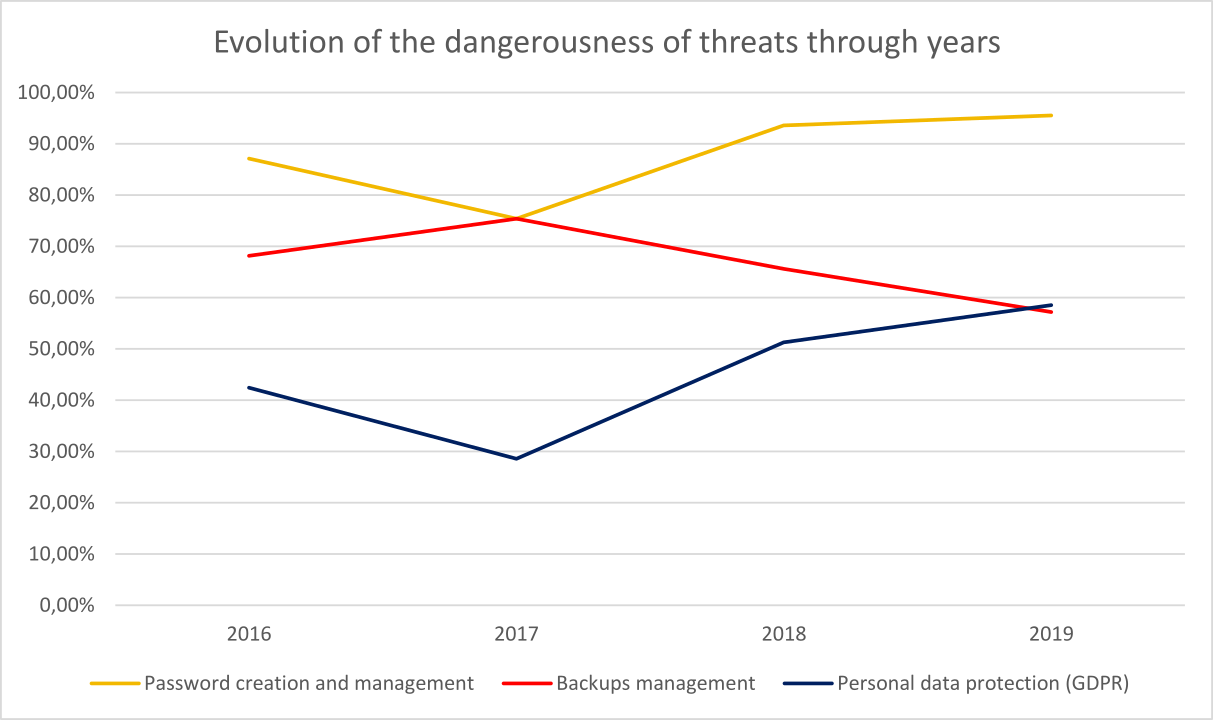
Line Graph 1 - The changes in 3 important threats over a 4-year period from 2016 to 2019
“Password creation and management” has always had the highest values, starting at 87.12% in 2016, dropping slightly to 75.40% in 2017, but growing in 2018 and culminating in 2019 with a threatening 95.53%.
The values of “Backups management” have been significantly lower, with the percentages of 68.18, 75.40, 65.59 and 57.19 for the years of 2016, 2017, 2018 and 2019, respectively. Although there was a peak in 2017, there has been a slight decrease in the following two years. Hopefully, this trend will continue in the future as well.
The threat related to personal data (GDPR) is a recent phenomenon, and as such, it should be treated with the utmost attention. The value of its dangerousness indicator was the lowest in 2017 (with a percentage of 28.57%). On the other hand, its trend is somewhat opposite of the one called “Backup management”. Unfortunately, it nearly doubled in 2018 (51.28%), and continued growing in 2019 (58.54%).
Conclusion
Technical means are often the first the first choices to secure an environment, and organisational means are often forgot despite the fact it’s more effective in information security field. Good practices and well-defined rules are often more effective than technical means, which stay essentials. Here some ideas that can help on importants points in information security:
- Passwords :
- https://www.nc3.lu/knowhow/glossary/Password.html
- https://www.youtube.com/watch?v=PdWoqcidb4g
- Security Charter :
- https://www.nc3.lu/knowhow/glossary/SecurityCharter.html
- Phishing :
- https://www.nc3.lu/knowhow/glossary/Phishing.html
- https://www.youtube.com/watch?v=FhsnUiFVv0k
- Backups :
- https://www.nc3.lu/knowhow/glossary/DataBackups.html
- https://www.youtube.com/watch?v=LAwJAJI0I5w
- https://www.youtube.com/watch?v=RUx1cHbqIIM
How can NC3 help?
NC3 (National Cybersecurity Competence Center) has multiple services available to the public. The goal is to give every organisation the necessary tools and information to define their risk maturity and improve it.
-
Fit4Cybersecurity: a self-assessment tool, to help business owners implement a better cybersecurity strategy. The objective of this free online survey is to assess the maturity of an organization in terms of applicable good practices in the field of information security. It is also a prerequisite for accessing the Diagnostic NC3: a minimum score of 65/100 is required.
-
NC3 Diagnostic: a NC3 expert visits your organization (in Luxembourg) and presents a 2-hour-long interview. The expert will identify vulnerabilities, evaluate the level of maturity concerning the security of your information, and will issue recommendations. A Fit4Cybersecurity is mandatory before accessing our service.
-
Monarc (Optimised Risk Analysis Method): a tool and method, allowing optimised, precise, and repeatable risk assessment. Monarc is a software application, which has been and is being developed by NC3. By using Monarc, you will be able to take appropriate measures to enhance information security within your organisation and meet your legal obligations.
-
Training: proper cybersecurity needs the foundation of good teamwork. NC3 training provides the knowledge and reflexes that your team requires. It is fully adaptable to your specific situation and encourages your staff to communicate better and follow the reflexes to fight against cyber threats more effectively.
-
TACOS (TrustApp NC3 for Obvious Security): a cybersecurity awareness application. It can teach user to be aware of cybersecurity risks and attacks with some articles, videos and tips and tricks.