2021 - I Quarterly Bulletin
NC3 TOP – Threat Observatory Platform
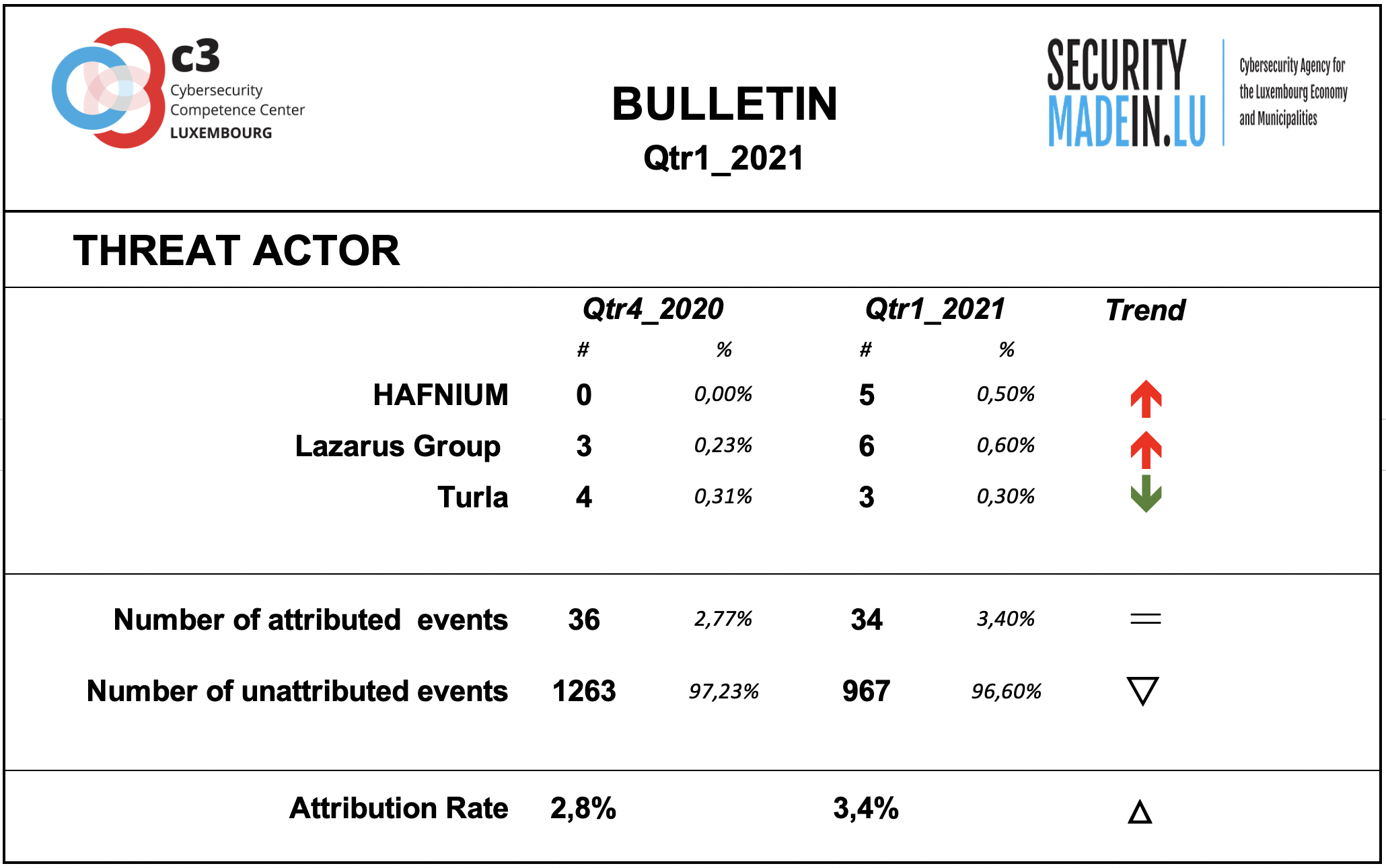
Threat Agent activities
Behind every cyber-attack there is an actor with a specific intent. However, for many events, the identity and general motivation are unknown. On the other hand, some groups have been well known for years and their criminal activities and techniques are documented and monitored. Typically, they conduct targeted attacks against specific organisations, using relatively sophisticated tools and attack procedures.
Some of them are considered as State-sponsored, but the actual link with various countries stays often subject of controversies and should be considered with prudence.
As during previous quarters, the attribution rate of events is very low. This means that most of the ongoing attacks are not attributable.
During this period, a new malware group, codenamed Hafnium, emerged.
The group engaged in a series of attacks using previously unknown exploits, targeting Microsoft Exchange servers. As is often the case in such cases, many other state actors and criminal groups will move quickly to exploit any system without patches. Applying today's patches promptly is the best protection against this attack.
According to the attribution found in the MISP records, the following groups were particularly active during this quarter:
HAFNIUM group is apparently operating from China. As documented by several security or IT organisations including Microsoft, it conducted a mass attack on Microsoft's Exchange software, which allowed to take control of many corporate servers, stealing e-mails, calendars, and any other sensitive information. The mass attack started in late February and early March. Thousands of companies fell victim. Many more were affected in the days following Microsoft's distribution of an emergency patch due to companies not updating their systems in time. The campaign was identified as a potential espionage mission due to the nature of the information stolen. Hafnium is believed to be affiliated with the Chinese State;
Lazarus group is a North Korean state-sponsored cyber threat group; it uses a wide range of methods depending on the characteristics of the campaigns carried out and the objectives pursued. It mainly aimed at manipulating employees of strategically important companies such as those involved in the military or aerospace industry;
MuddyWater is an Iranian threat group that has primarily targeted Middle Eastern nations, and has also targeted European and North American nations. The group's victims are mainly in the telecommunications, government (IT services), and oil sectors;
TA428 is a Chinese group that targeted a number of government agencies in East Asia overseeing government information technology, domestic affairs, foreign affairs, economic development, and political processes.
Turla is a Russian-based threat group specialised in espionage activities and intelligence gathering motivations, targeting organizations worldwide. It is suspected to be sponsered by Russian state; Turla’s espionage platform is mainly used against Windows machines, but has also been seen used against macOS and Linux machines;
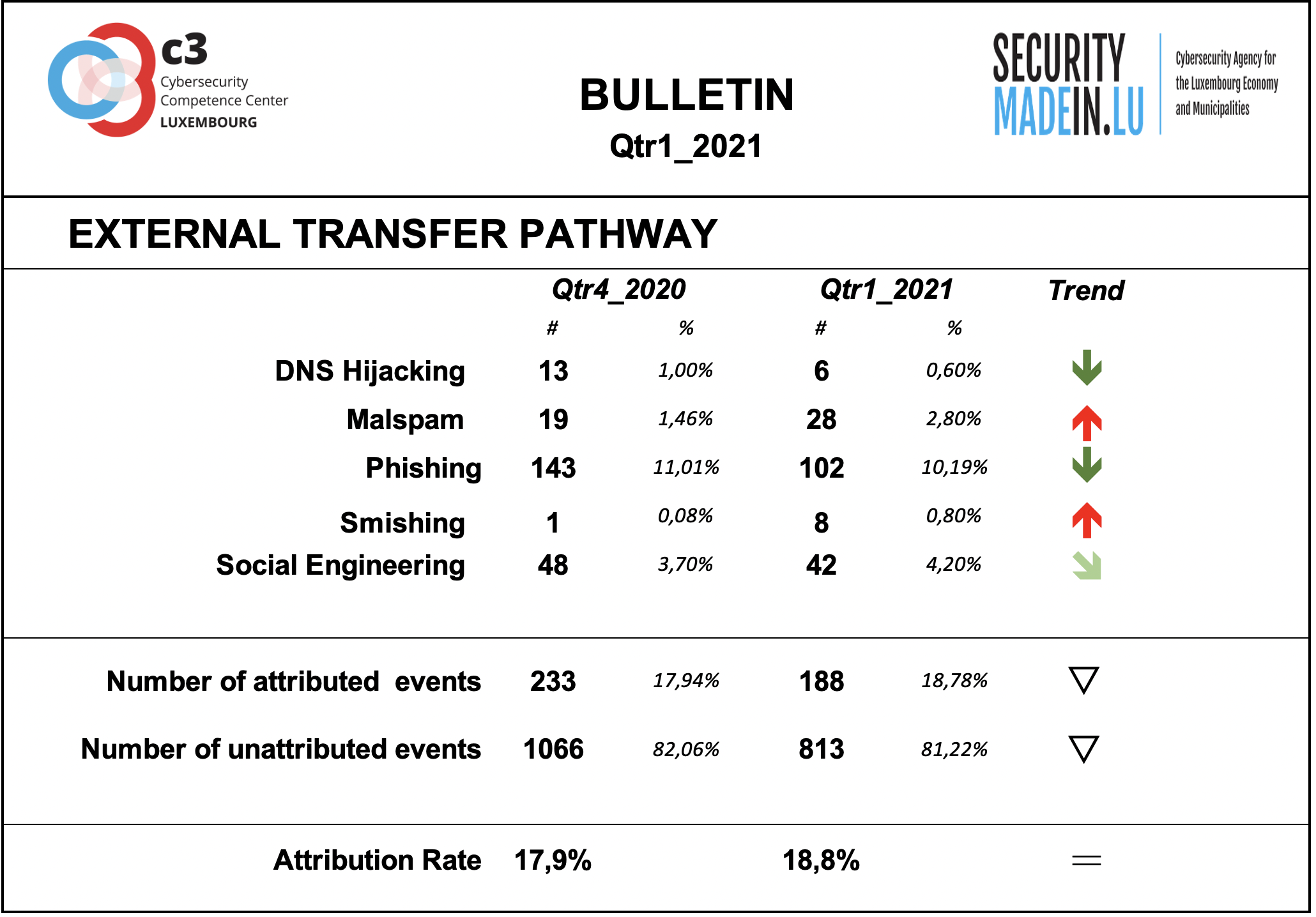
External transfer pathway and infrastructures
The transfer of the malicious artefacts or payloads is done through a number of different types of technical procedures and infrastructures.
Also, during the first quarter of 2021, it is confirmed that the most frequently used strategy is associated with scams that use email or similar approaches to reach potential victims.
Phishing is the most common strategy, but there has also been an increase in malspam and smishing events. In most of these cases, the pathway is a human to human or machine to human infrastructure.
The attribution rates are significantly better than for threat actors, even if still fairly low. Attribution means that it was possible to identify the external transfer pathway for a given event.
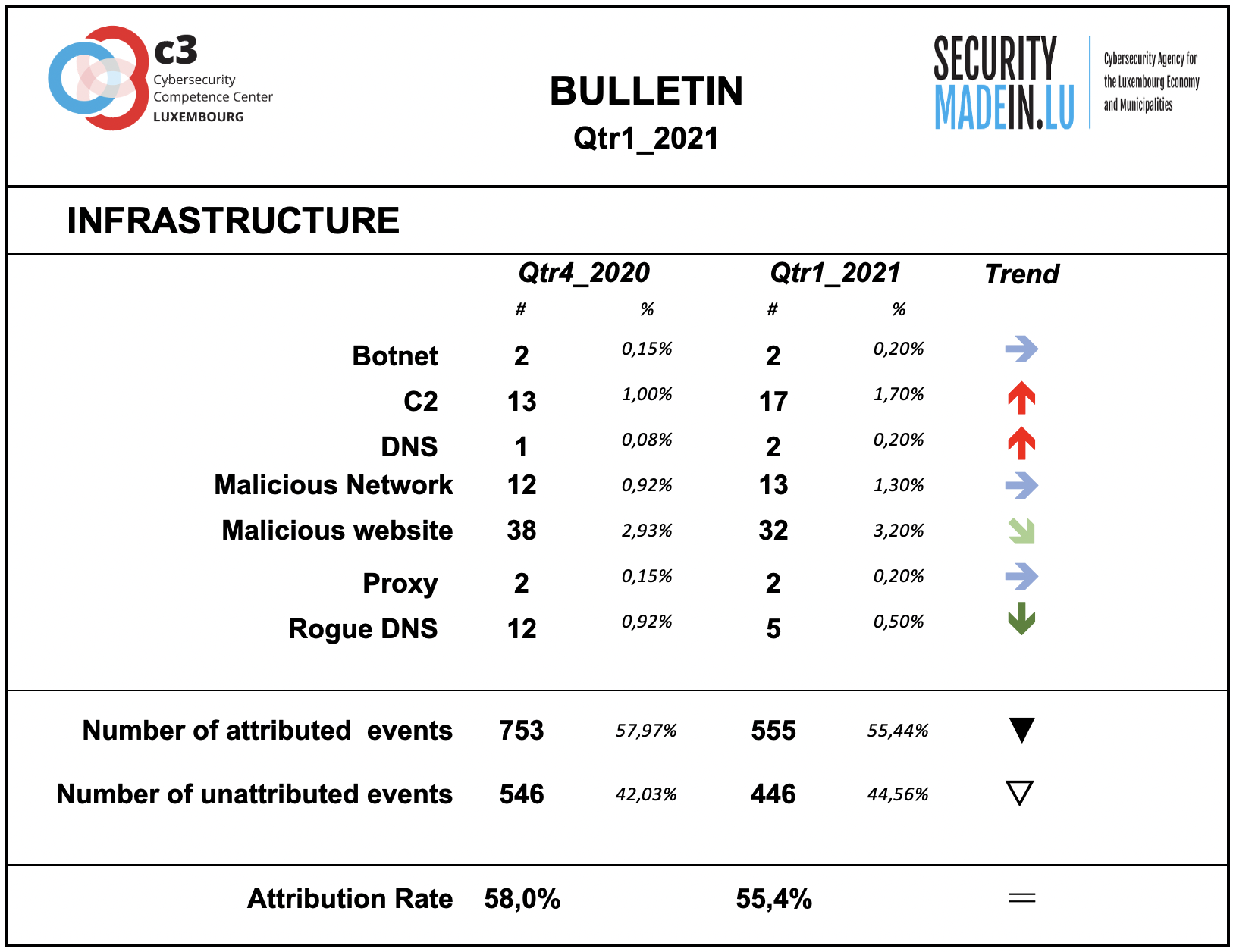
Infrastructures represent the type of systems being used for supporting attacks. Some are meant to compromise or help compromise, the targeted system, others are more focused on helping to maintain the foothold in it. Indeed, once access to a system device has been gained, a communication channel is maintained through the use of command and control (C2) infrastructures. The specific mechanisms vary greatly between attacks, but C2 generally consists of one or more covert communication channels between devices in a victim organization and a platform that the attacker controls. These communication channels are supporting the malicious activities. They are used to issue instructions to the compromised devices, download additional malicious payloads, and pipe stolen data back to the cyber-actor.
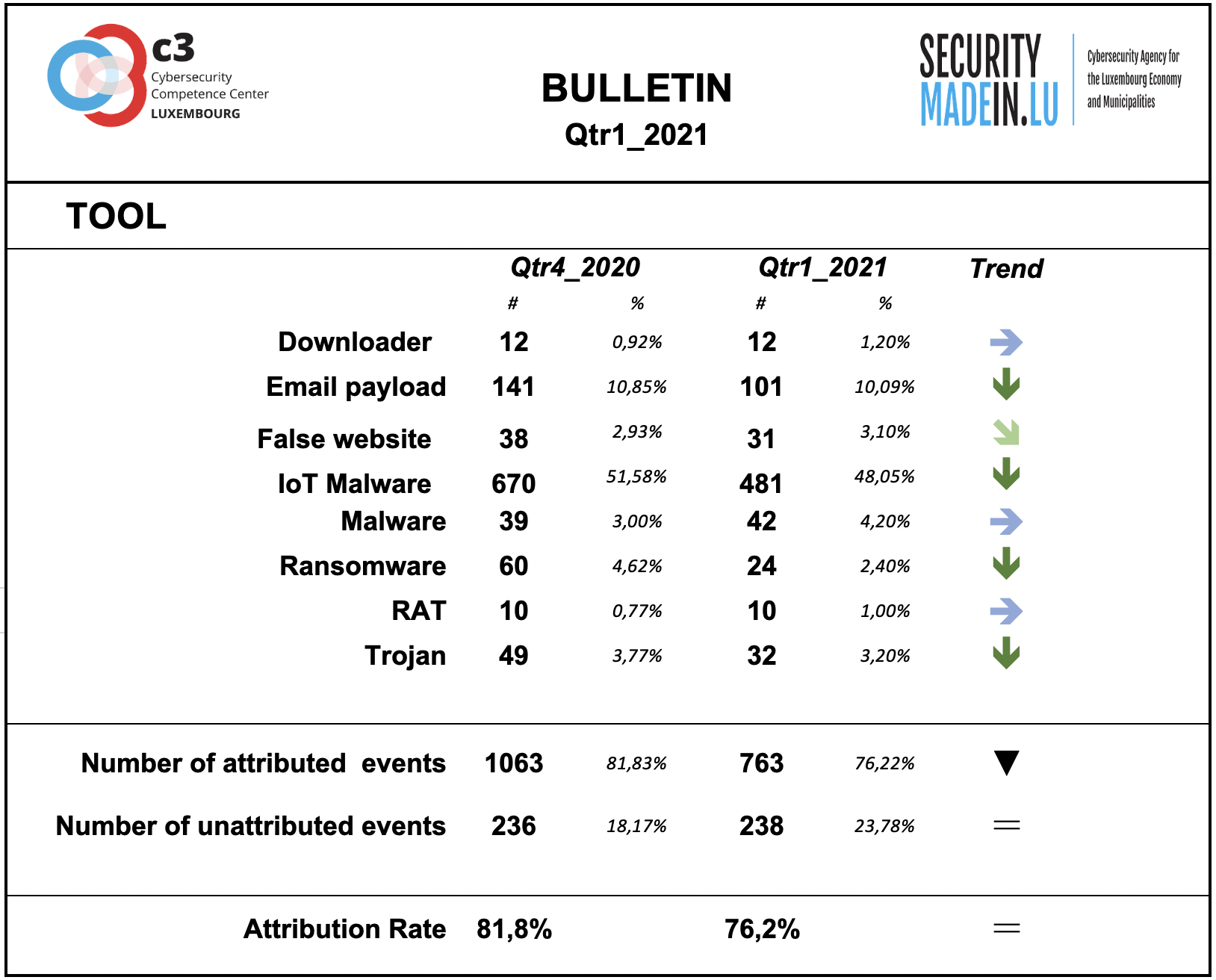
Tool
The monitoring system showed a substantial prevalence of the use of Malware especially associated with IoT systems.
During this quarter, there was a decrease in the number of ransomware attacks.
Compared to the other dimensions of the interpretation model, this dimension is confirmed as having the highest attribution rate.
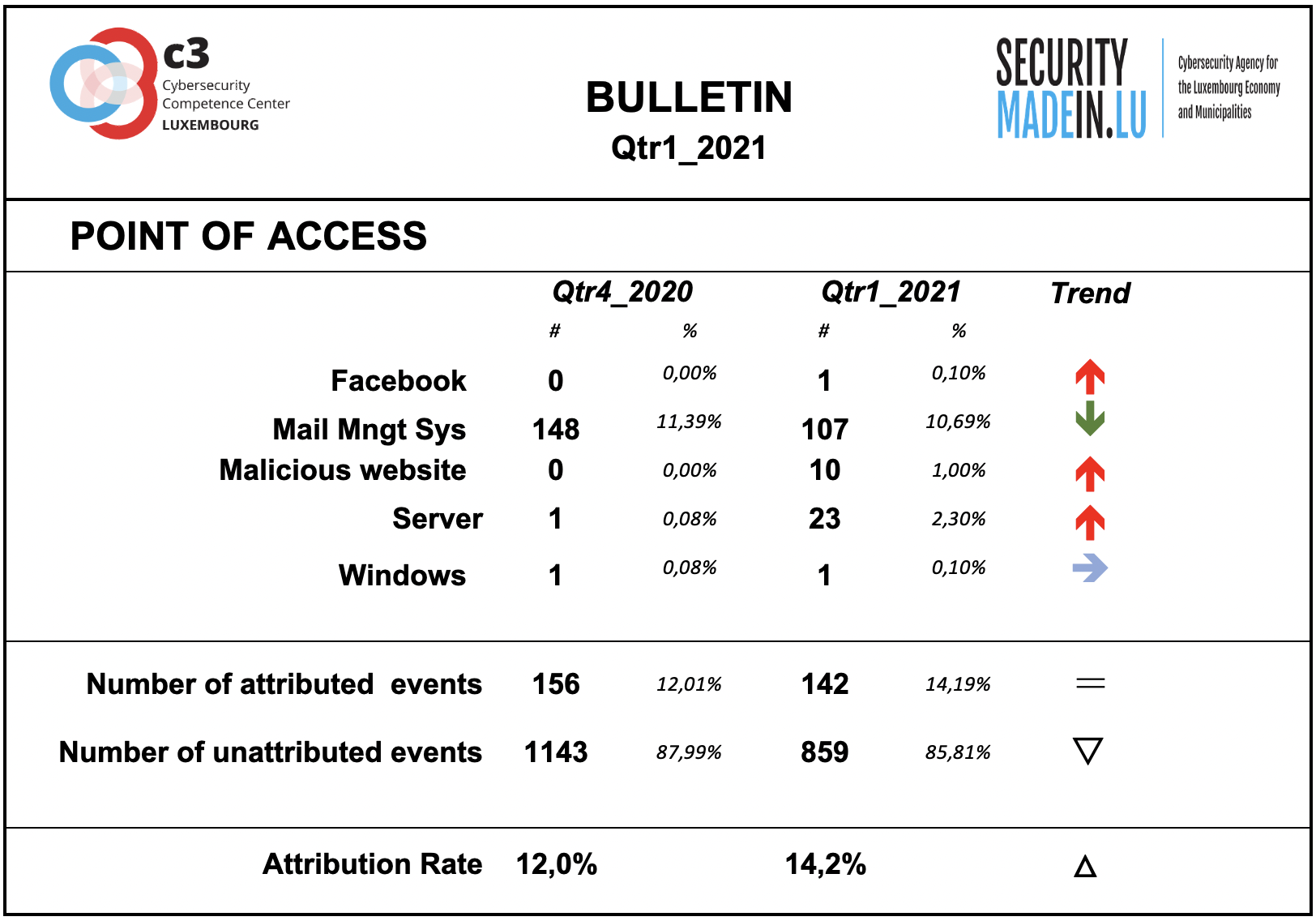
Points of access
The most common access point reported by MISPPRIV users is e-mail, which isn’t too surprising as it’s an effective ingress vector for several types of attacks. It’s often exploiting users’ weaknesses, be they voluntary (negligence) or involuntary (lack of knowledge about a specific threat.
However, it’s important to keep in mind that the attribution rate is rather low. Most of the attacks’ point of access is not known.
With regard to component and system vulnerabilities, the monitoring system identified the following:
the Firewall SonicWall SSLVPN SMA100
the router D-Link DIR-825
Microsoft Exchange Server
Accellion FTA (File Transfer Appliance)
Web browsers (Internet Explorer and Google Chrome)
McAfee Total Protection (MTP)
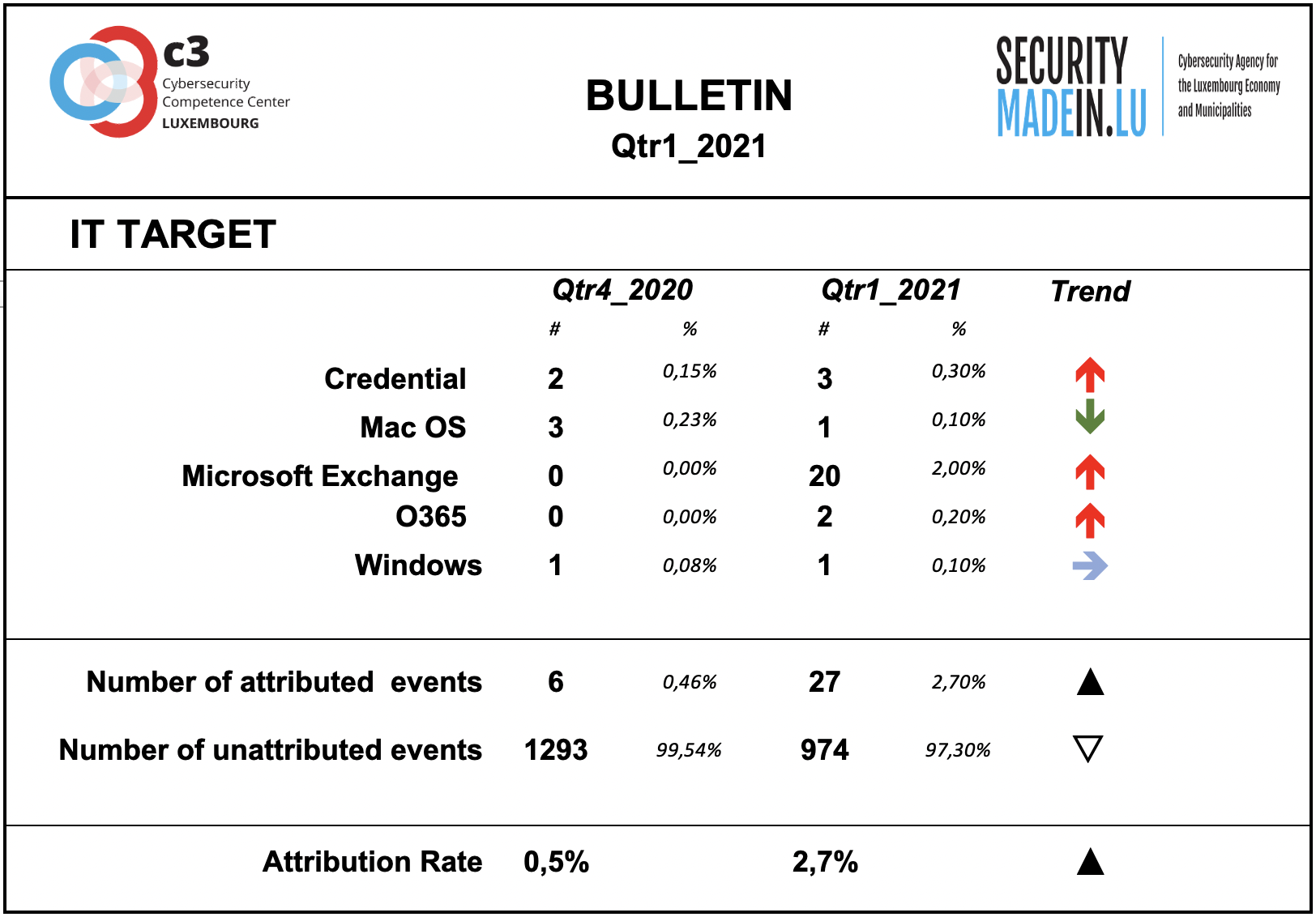
IT Target
Information on the attacked IT target is not sufficiently described by the analysed events.
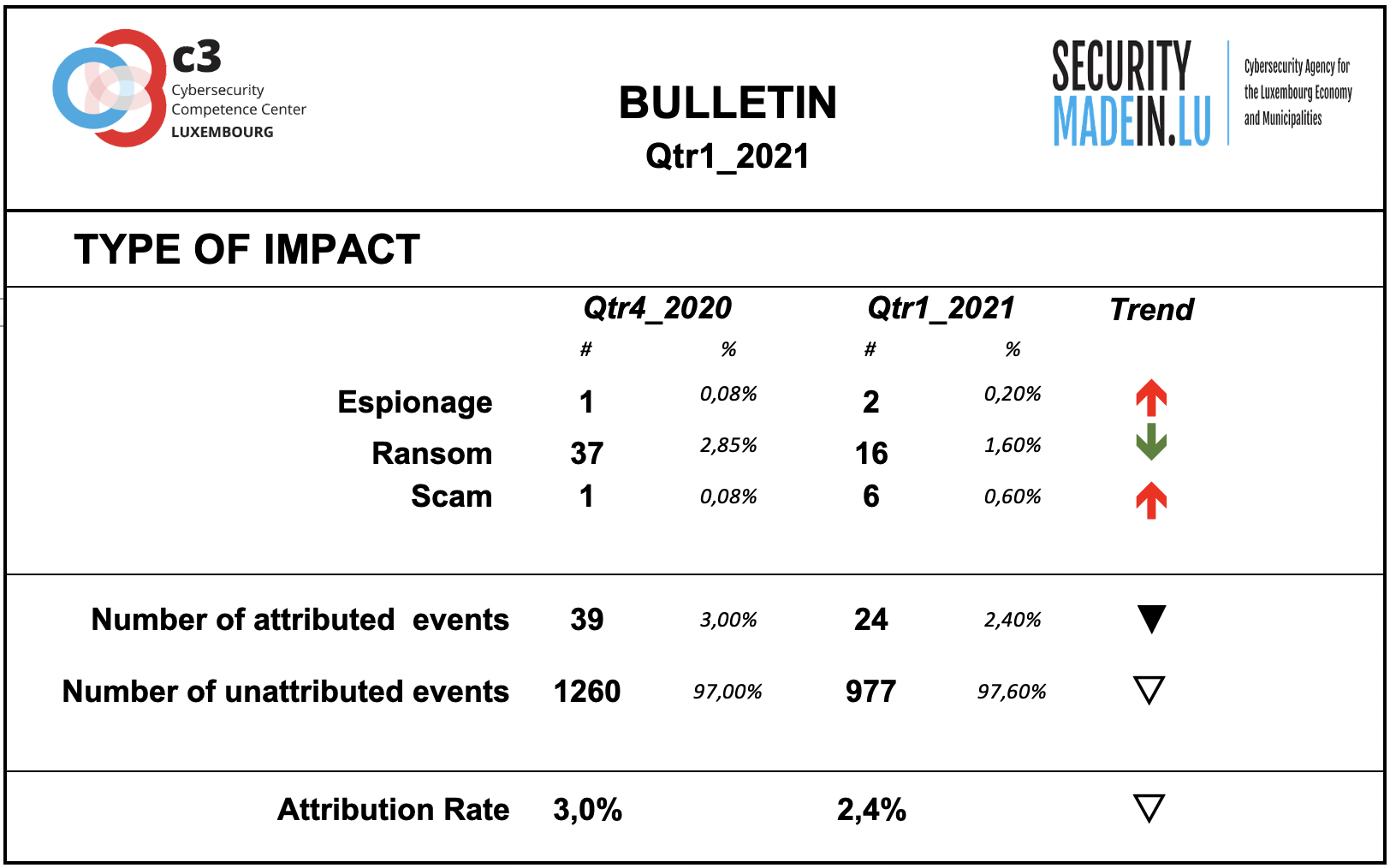
Type of Impact
Information on the type of consequences for the victim is mainly related to ransom demands, although fewer events were recorded than in the previous quarter.
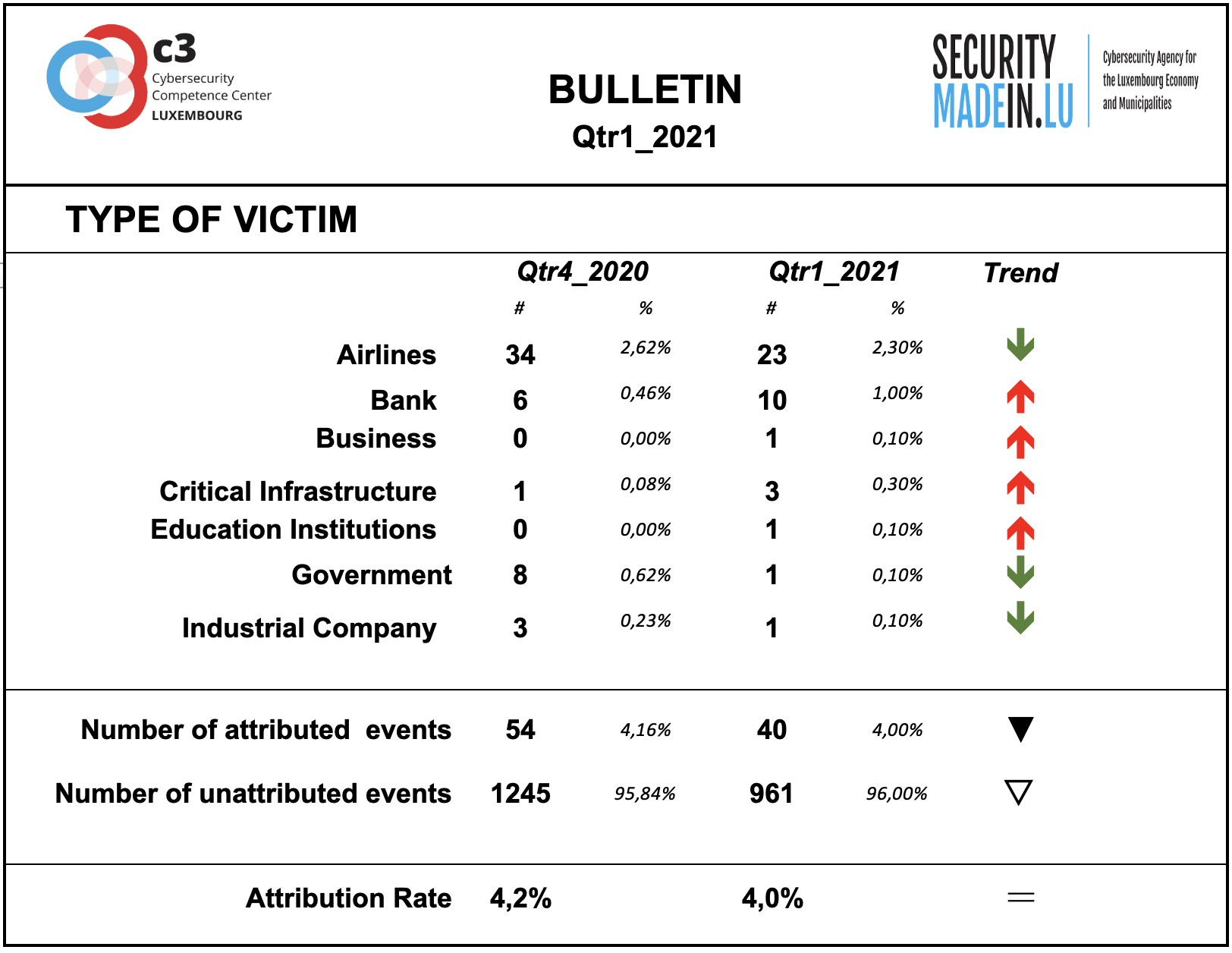
Type of Victim
There has been a continuation of attacks on airlines, although a decrease compared to previous quarters.
Attacks on banks and critical infrastructure systems are still in evidence.