The CISO Approach
In Brief
Securing information is far from being a technical issue for an organisation. Indeed, technical activities are only one aspect of an approach that, in order to be successful, must cover the activities of the company as a whole. Before putting in place procedures or technical measures to increase the safety of an organisation, it is important to carry out a risk analysis (risk management) and write a security policy.
The security policy is used to formalise and coordinate all organisational and technical security procedures of the organisation. Writing a security policy is a tedious task. We do not advise small businesses to approach them, instead, recommend moving forward with a view to continuous improvement: a short and concise document at a time, to gradually develop the sectoral procedures and policies that they have in place.
The common thread for the development of a security policy consists of one side in a set of good practices (ISO / IEC 27001 and ISO / IEC 27002), and the other in the analysis and risk assessment. Indeed, any organisation must ensure that behavioural, organisational and technical measures are put in place where they will be quickly and truly effective.
In any case, it is advisable to choose an approach adapted to the criticality size of the assets and the maturity of the organisation.
Security Charter
Defining and enforcing a security policy is the first step toward managing security. To ensure its success, it must meet the specific security needs of the organisation. A risk analysis, even a summary, must necessarily precede this process. Without this analysis, management will not be able to understand which assets to protect in priority. In order to prevent the most dreaded impacts, management needs to identify the most important threats as well as the vulnerabilities that are most easily exploited.
The implementation of a charter must be accompanied by a presentation to employees who will live with the measures proposed daily. Without training on their part, any charter risks being ignored, and thus losing its usefulness.
Security Policy
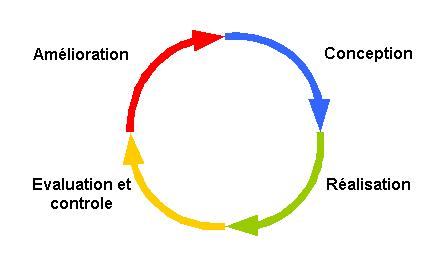 After the identification of the major risks for the organisation (risk management), the management can,
with a view to continuous improvement, go beyond ‘a simple security charter’. It will put in place a real
policy as well as specific procedures.
After the identification of the major risks for the organisation (risk management), the management can,
with a view to continuous improvement, go beyond ‘a simple security charter’. It will put in place a real
policy as well as specific procedures.
The implementation of a security policy, even rudimentary, will allow management to begin the organisation of security. It will be defined as formal procedures, the obligations and responsibilities of each, as well as processes related to the security of information.
It is not necessary at this stage to start with the implementation of a comprehensive security policy. Safeguarding an organisation is an ongoing process (Design, Implementation, Evaluation / Control and Improvement), implemented based on security measures, evaluated in Impact the most feared, threats the most likely and vulnerabilities the most important.
Design
This first step aims to correctly define the scope and context of the future system. It must also make it possible to identify and evaluate risks to develop a management plan. (It cannot, however, replace the risk analysis that must be done beforehand.)
The realisation step consists mainly of applying the security policy created in the previous step. Organisational and technical measures are put in place, behavioural measures are applied by staff.
Evaluation and Control
The evaluation systems must have been described in the safety manual. The goal is to ensure that the procedures put in place work as intended. These evaluations can be of several types:
- regular audits done as part of daily activities;
- automatic controls performed with software tools to create reports;
- comparison with other organisations;
- carrying out planned formal audits (‘risk assessment’);
- revision by the management.
If evaluations and controls reveal inadequacies in certain procedures, corrections must be made.
Improvement
The actions that will have been decided in the previous step will have to be implemented, i.e.:
- at the level of the security system itself, for example by appointing a (new) person responsible for all or part of the system;
- at the level of the operational procedures which will have been deduced, for example by the implementation of a different data backup procedure;
- at the tools level, such as the purchase of an antivirus tool.
Content of the Security Policy
The security policy should contain the following documents:
Section 1. Security Policy
Section 2. Security Organisation
- Assignment of Responsibilities
- Authorisation Procedure for Adding Information Processing Tools
- Tips from a Specialist
- Independent Review of Information Security
- Third-party Access and Outsourcing
Section 3. Classification and Resource Control
Section 4. Human Aspects
Section 5. Physical and Environmental Security
- Physical Security Perimeter
- Rules in Scope
- Electrical Equipment Safety
- Maintenance
- Off-Premise Security
- Disposal or Re-use of Equipment
- Offices in Order
Section 6. Operational Aspects and Communications
- Documented Procedures
- Separation of Development and Production Environments
- External Resource Management
- Protection Against Malware
- Data Backup
- Media Security During Transport
Section 7. Access Control
- Access Control Policy
- Access Rights Management
- Password Management
- Using External Networks
- Connecting from the Outside
- Network Separation
- Login Procedure
Section 8. Systems Development and Maintenance
Section 9. Security Incident Management
- Reporting Events Related to Information Security
- Incident Management and Information Security Enhancements
- Analysis of Obligations with Obligations